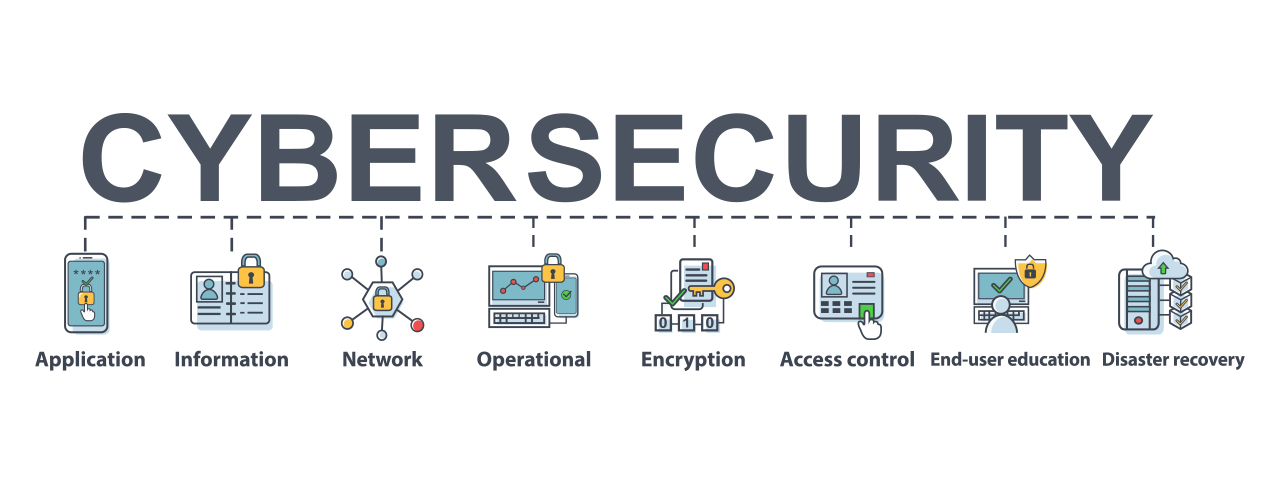
A multi-layer cybersecurity strategy is the most effective means to combat any serious cyber attack. A combination of firewalls, software application as well as a range of tools will certainly assist deal with malware that can influence everything from mobile phones to Wi-Fi. Below are several of the ways cybersecurity experts fight the onslaught of electronic strikes.
The Basic Principles Of Cyber Security Consulting
VPNs produce a safe network, where all information sent out over a Wi-Fi connection is encrypted.
Fascination About Cyber Security Consulting
Protection made application help in reducing the hazards and great site make certain that when software/networks stop working, they fail risk-free (Cyber Security Consulting). Strong input recognition is commonly the very first line of defense versus various kinds of injection assaults. Software program advice as well as applications are created to approve user input which opens it as much as strikes and right here is where solid input recognition helps strain harmful input hauls that the application would process.
Something went wrong. Wait a minute and also try once again Attempt once again.